Fishing Traps in the Crypto Airdrop Tutorial

Author: Bitrace
Airdrops are marketing events in which DeFi protocols distribute tokens for free to early active community members as a way to reward their early support and encourage continued use of the protocol.
For example, on March 23rd, the Layer 2 protocol Arbitrum conducted an airdrop in which 625,000 individual active wallets received nearly 1.16 billion $ARB tokens, with each address receiving between 625 and 10,250 tokens. Based on the $ARB price of $1.63 at the time, each address received between $7,000 and $114,900 worth of tokens. The wealth effect of $ARB attracted more newcomers to join the army of people trying to get airdrops. However, due to newcomers’ lack of experience with on-chain protocols and unclear background and positions of unreleased projects, it can be challenging to predict a project’s token release time, expectations, and the interaction rules for airdrops.
To guide these newcomers, KOLs started writing airdrop tutorials. Consequently, various airdrop tutorials came, simultaneously giving space to numerous malicious actors providing phishing links under the guise of these tutorials.
According to the victim, they saw a message in a group chat about “ArbitrumSwap 1000 limited OAT with airdrop expectations” and clicked on the link to follow the tutorial and interact with the project. As a result, the victim’s USDT permissions were granted to a high-risk contract, and 5000 USDT was stolen. Currently, Arbitrum_Swap has closed its social media accounts and website. However, it is difficult to estimate the scope and speed of the dissemination of the airdrop tutorial in this situation. Once it is shared through group chats, it is extremely difficult to retract and remedy the situation.

After tracking the on-chain situation, it was discovered that the ArbitrumSwap tutorial scam has caused financial losses to 67 addresses, with a total of 158,045.64 USDT stolen.
Coincidentally, similar scams have also appeared on other social platforms. On April 18th, a KOL guides users to interact with the Orbiter cross-chain bridge but embeds a phishing website in the tutorial. The real website for the protocol is orbiter.finance, while the phishing tutorial uses orblter.finance.
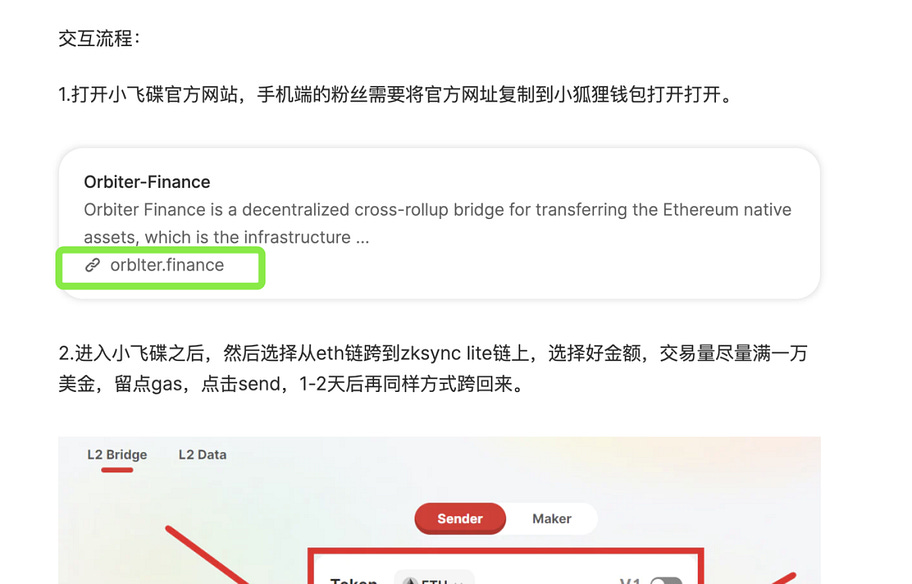
Due to the large reader base of this scammer, as of the incident, more than 30 ETH in losses have occurred. Currently, the KOL has deleted their personal account, and Bitrace is assisting some Chinese victims in reporting the case to police.
Airdrop Scam Technique Analysis
Essentially, airdrop tutorial scams are still phishing scams. Their methods involve guiding unsuspecting airdrop participants step-by-step into phishing websites, interacting with high-risk contracts to deceive victims into granting token permissions, and then using these permissions to steal tokens.
In traditional phishing scams, malicious links often appear as counterfeit websites mixed in search engines, emails, and social media. Ordinary users usually have a high ability to identify these types of scams. However, in this type of scam, phishing websites are secretly embedded in airdrop tutorials, catching users off guard and targeting web3 newcomers who follow instructions without question.
1、Bitrace reminds you that interacting with on-chain protocols involves risks. Here are some important points to keep in mind:
2、Verify the accuracy of official websites by cross-checking multiple sources. Do not blindly trust search engine website certifications.
3、Be cautious about believing airdrop tutorials and website links posted on the internet.
After interacting with an unknown contract, cancel relevant authorizations as soon as possible.
4、Separate your wallets: Use a dedicated wallet for large assets and only interact with other contracts using your everyday wallet.
Follow us
Twitter: https://twitter.com/WuBlockchain
Telegram: https://t.me/wublockchainenglish
Comments
Post a Comment